假设攻击端为10.0.0.1,接收端口为8080
服务器端为10.0.0.2
1、Bash
关于bash中的重定向知识,可以参考shell之后的操作
服务器端:
|
|
|
|
攻击端:
|
|
2、NetCat
服务器端
|
|
现在的很多/bin/nc -> /etc/alternatives/nc -> /bin/nc.openbsd
但是实际上这个nc.openbsd不支持nc -e命令
所以我们最好使用的是/bin/nc.traditional
|
|
当然若没有/bin/nc.traditional这个nc传统版,我们也可以使用下面的方法:
|
|
|
|
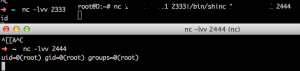
|
|
3、PHP
|
|
不知道怎么回事,这个反弹的shell并不能用。代码假设TCP连接的文件描述符为3,如果不行可以试下4,5,6。当然推荐使用下面的:
|
|
或者
|
|
4、Python
以python2.7为例
|
|
|
|
|
|
5、Ruby
|
|
不依赖于/bin/sh的
|
|
windows环境下
|
|
MSF中的相应的反弹shell代码
|
|
6、Perl
|
|
一个不依赖调用/bin/bash的方法
|
|
完整的perl反弹shell脚本
|
|
|
|
7、Java
ReverseShell.java
|
|
值得一提的是,由于java并不是脚本式语言,所以并不支持直接运行一行程序!所以需要进行的操作是:
先将上述内容复制到一个文件中,以ReverseShell.java命名(必须是这个名字,类和文件名要一致);
然后运行javac ReverseShell.java生成ReverseShell.class字节码文件。(这个操作需要javac,该命令依赖jdk)
最后执行java ReverseShell(执行过程中不用加后缀,java命令依赖于jre,最好将其放置在后台运行。即加上&或者nohup)
下面提供一个相对较为完整的Applet程序,其应该在网页中运行的,但是为了测试简单,我们直接在其中加入了main函数,所以有点像一个单独的程序一样。
|
|
运行此程序之前,应该更改环境变量的设置
8、Lua
|
|
不建议安装最新的lua,因为会出现以下问题
|
|
这个时候,你应该查看一下服务器上的/usr/local/share/lua下的目录到底是5.1还是5.2,根据其版本,安装正确的lua
9、Jsp
|
|
reverse_shell.jsp
|
|
10、正向shell(nc为例)
服务器端(有的nc版本不支持-e,这个时候你可以参考NetCat)
|
|
攻击端
|
|
最后要说的是xterm,这是一个session,可以维持;而由于服务器上和本地都得装相应的程序,所以起来较为麻烦!